Introduction:
While this article focuses on the installation and configuration aspects of SFTP via the application named ProFTPd on the CentOS 8 platform, it’s also necessary to gain a cursory perspective on the list of common protocols in this space prior to proceeding to the technical details of the subject.
File Transfer Protocols Overview:
FTP
- – File Transfer Protocol
- – Default ports: 20/TCP (data), 21/TCP (command/control), and passive outgoing ports (typically 1026-65535)
- – Encryption: none
- – Requires permissive firewalls that does not restrict outgoing traffic by port
TFTP
- – Trivial File Transfer Protocol
- – Default port: 69/UDP file transfers, TCP/8099 user interface
- – Encryption: None
- – Faster than FTP
FTPS
- – File Transfer Protocol Secured (FTP over TLS)
- – Default ports: 21/TCP for incoming sessions, 990/TCP for handshake, 989/TCP data transmission, and dynamic outgoing ports (typically 49152-65535 TCP/UDP)
- – Encryption: option to encrypt one or both command and data channels using SSL/TLS (SSL certificate)
- – Separates the control channel from data channel (multiple ports). This makes it difficult to restrict firewall traffic by ports
SCP
- – Secured Copy Protocol
- – Default port: 22/TCP for both incoming sessions and data transfer.
- – Uses SSH to secure the session where the server publishes a public key and the client verifies it with its private key.
- – Encryption: enabled on both authentication information and data files being transferred.
– Basic features: can write to remote directory, cannot list remote directories or removing files by default - – Faster than SFTP due to a more efficient transfer algorithm that does not require packet acknowledgements.
- – SCP is available as long as SSH is running on a server. Hence, it is possible to have both SCP (port 22) and SFTP (custom port such as 8282) running on the same server as separate daemons.
SFTP
- – Secured File Transfer Protocol (SCP with packets acknowledgement and advanced management functions)
- – Default port: 22/TCP for both incoming sessions and data transfer. Similar to SCP and often shares SSH RSA/DSA machine keys.
- – Encryption: it is the same as SCP
- – Advanced features: protocol includes functions to control file access, transfer, and management (e.g. disable traversal outside of home or designated directory)
- – Although slower transfer speed than SCP, all packets are verified to ensure data consistency.
Deliverable
The finished build will include a Linux machine with the two software titles as shown below:
[moi@testbox authorized_keys]# cat /etc/redhat-release
CentOS Linux release 8.1.1911 (Core)
[moi@testbox]# proftpd --version
ProFTPD Version 1.3.6c
These shall be these settings:
- SFTP default port shall be changed from its default of 21/TCP to 8282/TCP
- FTP & FTPS disabled in ProFTPd. Hence, no SSL certs are required.
- Authentication shall be based on the server’s SSH RSA/DSA keys, combined with local Linux users database.
- Users will not be able to traverse outside of their
/home/%udirectories - Root and anonymous will be blocked from using SFTP
Part 1: Installation
# Add EPEL repo - the easy way
sudo yum install -y epel-release
# Optional: adding EPEL repo - the kinda ez way
# sudo dnf install -y https://dl.fedoraproject.org/pub/epel/epel-release-latest-8.noarch.rpm
# Just for kicks, these lines would suffice for Ubuntu - too easy
# Lubuntu 20.04 with ProFTP
# sudo apt -y install proftpd
# Install ProFTP
sudo yum install -y proftpd proftpd-utils
sudo systemctl start proftpd
sudo systemctl enable proftpd
# Set firewall
openPort=8282 # Usage of obscured port as an effort to elude port-scanners
sudo firewall-cmd --zone=public --add-service=ftp --permanent
sudo firewall-cmd --zone=public --add-port=$openPort/tcp --permanent
sudo firewall-cmd --reload
sudo firewall-cmd --zone=public --list-ports
sudo firewall-cmd --zone=public --list-services
# Validate the instance of proftpd
[cuilo@web02 ~]$ service proftpd status
Redirecting to /bin/systemctl status proftpd.service
● proftpd.service - ProFTPD FTP Server
Loaded: loaded (/usr/lib/systemd/system/proftpd.service; enabled; vendor preset: disabled)
Active: active (running) since Wed 2020-05-27 10:37:05 PDT; 29s ago
Main PID: 5999 (proftpd)
Tasks: 1 (limit: 23590)
Memory: 4.1M
CGroup: /system.slice/proftpd.service
└─5999 proftpd: (accepting connections)
May 27 10:37:05 web02 systemd[1]: Starting ProFTPD FTP Server...
May 27 10:37:05 web02 proftpd[5997]: Checking syntax of configuration file
May 27 10:37:05 web02 proftpd[5997]: 2020-05-27 10:37:05,665 web02 proftpd[5997]: processing configuration d>
May 27 10:37:05 web02 systemd[1]: Started ProFTPD FTP Server.
May 27 10:37:05 web02 proftpd[5999]: 2020-05-27 10:37:05,773 web02 proftpd[5999]: processing configuration d>
May 27 10:37:05 web02 proftpd[5999]: 2020-05-27 10:37:05,840 web02 proftpd[5999] 192.168.100.6: ProFTPD 1.3.>
Part 2: Configuration
# Set ServerName and turn software identity off
sudo vim /etc/proftpd.conf
###############################################
ServerName "sftp.DOMAIN.URL" # set server name
ServerIdent Off # Hide ProFTP version
#<IfDefine TLS> # Disable FTPS by commenting these lines out
#Include /etc/proftpd/mod_tls.conf
#</IfDefine>
###############################################
# Optional:
UseIPv6 off # Turn off IPv6 if not needed
MasqueradeAddress x.x.x.x # Masq the FTP server address as its public IP
DefaultRoot /home/%u[0]/%u # Assign users to their home directories (e.g. /home/b/jimmybond)
###############################################
# add 'anonymous' into the prohibited FTP users list
echo 'anonymous' >> /etc/ftpusers
# Create a custom config file to change default port 21 to 8282
sudo vim /etc/proftpd/conf.d/modsftp.conf
# OR
sudo bash -c "cat <<EOF > /etc/proftpd/conf.d/modsftp.conf
###############################################
LoadModule mod_sftp.c # These modules are not loaded by default
LoadModule mod_sftp_pam.c # Hence, these lines must be here
<IfModule mod_sftp.c>
SFTPEngine on
Port 2222
SFTPLog /var/log/proftpd/sftp.log
# Configure the RSA host keys,
# using the same host key files as OpenSSH
SFTPOptions InsecureHostKeyPerms # This allows usage of insecure protocols (e.g. SHA256)
SFTPHostKey /etc/ssh/ssh_host_dsa_key
SFTPHostKey /etc/ssh/ssh_host_rsa_key
#SFTPHostKey /etc/ssh/ssh_host_ecdsa_key
#SFTPHostKey /etc/ssh/ssh_host_ed25519_key
# Enable compression
SFTPCompression delayed
# Auth methods
SFTPAuthMethods password
# SFTPAuthMethods publickey # Uncomment if using key-based authentication
# SFTPAuthorizedUserKeys file:/etc/proftpd/authorized_keys/%u # Uncomment if using public key
# SFTP specific configuration
DefaultRoot ~ !adm
</IfModule>
###############################################
EOF"
# ProFTPd sftp_mod relies on SSH2, which requires both DSA and RSA keys
# RSA is present by default, DSA could be manually generated using an existing RSA private key with this command
ssh-keygen -f /etc/ssh/ssh_host_dsa_key -N '' -t dsa
# Set the correct permissions for dsa & rsa keys
chmod 600 /etc/ssh/ssh_host_dsa_key
chmod 600 /etc/ssh/ssh_host_rsa_key
Optional: create authorized keys (if not using password auth)
username=test
sudo mkdir /etc/proftpd/authorized_keys
sudo ssh-keygen -e -f /$username/.ssh/authorized_keys | sudo tee /etc/proftpd/authorized_keys/$username
sudo ssh-keygen -e -f /$username/.ssh/id_rsa.pub | sudo tee /etc/proftpd/authorized_keys/$username
# Optional: disable SFTP Access on SSH
# WARNING: do not perform this if users are connecting SFTP via port 22 (SSH)
sed '/^#/! {/sftp/ s/^/#/}' -i /etc/ssh/sshd_config
# Undo previous command
sed -i '/sftp/s/^#//g' /etc/ssh/sshd_config
systemctl restart sshd
# Config SELinux to allow proftpd full system access
setsebool -P ftpd_full_access 1
#setsebool -P ftpd_full_access 0 # reverse
# Optional: convert SSH RSA key to RFC4716 format
#######################
ftpKeysDirectory=/etc/proftpd/authorized_keys
mkdir $ftpKeysDirectory
ssh-keygen -e -f /etc/ssh/ssh_host_rsa_key >> $ftpKeysDirectory/ssh_host_rsa_key_RFC4716_format
ssh-keygen -e -f /etc/ssh/ssh_host_rsa_key.pub >> $ftpKeysDirectory/ssh_host_rsa_key_RFC4716_pub
# then add this to config
vim /etc/proftpd/conf.d/modsftp.conf
SFTPAuthorizedUserKeys file:/etc/proftpd/authorized_keys/%u
#######################
# Set timeout values
sudo vim /etc/proftpd.conf
### Insert these statements in the 'Globals' section
TimeoutNoTransfer 0
TimeoutStalled 0
TimeoutIdle 0
# restart proftp daemon
systemctl restart proftpd
Part 3: validate that SFTP works
# Create a test user
username=tupacshakur
password=thepoet #https://blog.kimconnect.com/powershell-generate-random-password/
useradd -m -d /home/$user/ -s /bin/bash $username -p $(openssl passwd -1 $password)
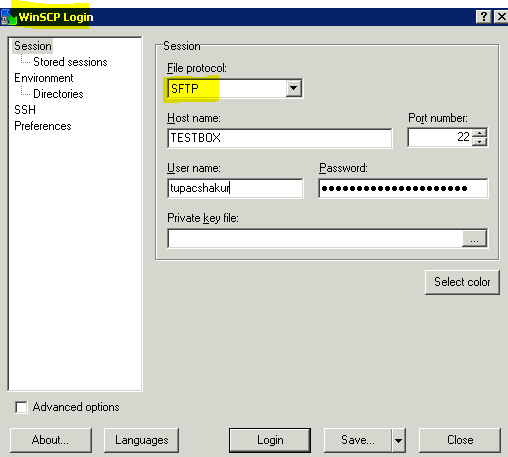
Filezilla FTP Client
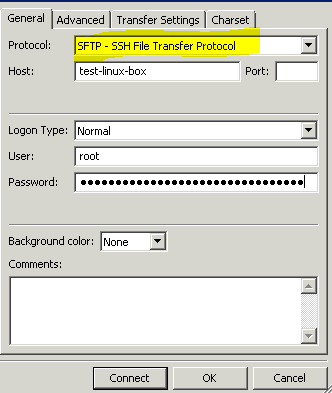
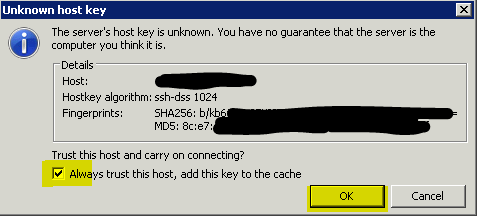
Linux sftp client:
# Proftpd v0.11.1 appears to be using a DSA host key, which is deprecated on modern SSH clients in favor of RSA. Hence, this error would occur:
# Unable to negotiate with 500.500.500.5000 port 8282: no matching host key type found. Their offer: ssh-dss
# Here's how to bypass:
[coco@linux007 ~]# sftp -P8282 -oHostKeyAlgorithms=+ssh-dss 500.500.500.500
The authenticity of host '[500.500.500.500]:8282 ([500.500.500.500]:8282)' can't be established.
DSA key fingerprint is SHA256:b/loremipsumetalsitmetbazroofoohashbar.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[500.500.500.500]:8282' (DSA) to the list of known hosts.
Recommended: Active Security with Fail2Ban & FirewallD
Fail2ban
… just go here …
FirewallD
Basic configuration example:
# Check active zones
# The example output below means that there's only 1 external zone for this server
# virbr0 is a loopback interface
[root@linux1 ~]# firewall-cmd --get-active-zones
libvirt
interfaces: virbr0
public
interfaces: eth0
# Get default zone - verify the output above
[root@linux1 ~]# sudo firewall-cmd --get-default-zone
public
# Get current config of default zone
[root@linux1 ~]# sudo firewall-cmd --zone=public --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0
sources:
services: cockpit dhcpv6-client ftp ssh
ports: 8282/tcp
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
# Add services to default zone - use each line as needed
sudo firewall-cmd --zone=public --permanent --add-service=ftp
sudo firewall-cmd --zone=public --permanent --add-port=8282/tcp # where 8282 is an obscured port for ftp services
sudo firewall-cmd --zone=public --permanent --add-service=ssh
sudo firewall-cmd --zone=public --permanent --add-port=22/tcp
# reload firewalld to realize changes
sudo firewall-cmd --reload
Advanced illustration:
# Edit the internal zone to restrict accesses
firewall-cmd --zone=internal --permanent --add-service=ssh
firewall-cmd --zone=internal --permanent --add-service=proftpd
firewall-cmd --zone=internal --permanent --add-source=x.x.x.x/32 # 1 specific IP
firewall-cmd --zone=internal --permanent --add-source=x.x.x.x/29 # 6 IPs from certain range
firewall-cmd --zone=internal --permanent --add-source=x.x.x.x/24 # 254 IPs from certain range
# Transition the default inface from being associated with the public zone to the internal zone - this also has the effect of making the internal zone 'active'
defaultInterface=$(firewall-cmd --zone=public --list-interfaces)
firewall-cmd --zone=internal --change-interface=$defaultInterface
# Optional: remove overlapping services from the public zone
firewall-cmd --zone=public --remove-service=ssh
firewall-cmd --zone=public --remove-service=proftpd
Troubleshooting:
# Check passive ports
sed -n '/\<Global/,/\/Global/p' /etc/proftpd.conf /etc/proftpd/conf.d/* | grep PassivePorts
# Check whether SFTP Access has been granted on SSH Port
[cuilo@testbox]# grep sftp /etc/ssh/sshd_config
Subsystem sftp /usr/libexec/openssh/sftp-server
# Check daemon & listening ports
netstat -tlpn| grep ftp
[cuilo@testbox ~]# netstat -tlpn| grep ftp
tcp6 0 0 :::21 :::* LISTEN 9853/proftpd: (acce
# Check service account, listening port, and process ID
[cuilo@testbox ~]# ss -tlpn | grep ftp
LISTEN 0 128 *:21 *:* users:(("proftpd",pid=10036,fd=0))
# Check what process is listening on a particular port
lsof -Pi :21 -sTCP:LISTEN
# Check firewall rules
[cuilo@testbox ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0
sources:
services: cockpit dhcpv6-client ftp ssh
ports: 8282/tcp
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
# FTP status
systemctl status proftpd
# Check SELinux's permissions for ftp
[root@testbox]# getsebool -a | grep ftp
ftpd_anon_write --> off
ftpd_connect_all_unreserved --> off
ftpd_connect_db --> off
ftpd_full_access --> on
ftpd_use_cifs --> off
ftpd_use_fusefs --> off
ftpd_use_nfs --> off
ftpd_use_passive_mode --> off
httpd_can_connect_ftp --> off
httpd_enable_ftp_server --> off
tftp_anon_write --> off
tftp_home_dir --> off
# Tail the log
tail -f /var/log/proftpd/sftp.log
2040-02-30 20:03:59,967 mod_sftp/1.0.0[11680]: no available host keys, unable to handle session
# This was resolved by adding the DSA key
# Often, new system setups should include this script to regenerate DSA keys
###############################################
#!/bin/sh
# regen-dsa-key.sh
keygen=/usr/bin/ssh-keygen
if [ ! -f /etc/ssh/ssh_host_dsa_key ]; then
$keygen -q -t dsa -f /etc/ssh/ssh_host_dsa_key -N '' \
-C '' < /dev/null > /dev/null 2> /dev/null
echo "/etc/ssh_host_dsa_key has been regenerated"
fi
exit 0
###############################################
# Check passive ports
sed -n '/\<Global/,/\/Global/p' /etc/proftpd.conf /etc/proftpd/conf.d/* | grep PassivePorts
# Check whether SFTP Access has been granted on SSH Port
[cuilo@testbox]# grep sftp /etc/ssh/sshd_config
#Subsystem sftp /usr/libexec/openssh/sftp-server
# Check daemon & listening ports
netstat -tlpn| grep ftp
[cuilo@testbox ~]# netstat -tlpn| grep ftp
tcp6 0 0 :::21 :::* LISTEN 9853/proftpd: (acce
# Check service account, listening port, and process ID
[cuilo@testbox ~]# ss -tlpn | grep ftp
LISTEN 0 128 *:21 *:* users:(("proftpd",pid=10036,fd=0))
# Check what process is listening on a particular port
lsof -Pi :21 -sTCP:LISTEN
# Check firewall rules
[cuilo@testbox ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0
sources:
services: cockpit dhcpv6-client ftp ssh
ports: 8282/tcp
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
Problem with incorrect permissions to DSA/RSA files:
Symptom:
[root@sftp backupadmin]# systemctl status proftpd -l
● proftpd.service - ProFTPD FTP Server
Loaded: loaded (/usr/lib/systemd/system/proftpd.service; enabled; vendor preset: disabled)
Active: active (running) since Thu 2018-05-12 10:01:36 PST; 10min ago
Process: 236976 ExecReload=/bin/kill -HUP $MAINPID (code=exited, status=0/SUCCESS)
Process: 79731 ExecStartPre=/usr/sbin/proftpd --configtest (code=exited, status=0/SUCCESS)
Main PID: 79735 (proftpd)
Tasks: 1 (limit: 49018)
Memory: 2.7M
CGroup: /system.slice/proftpd.service
└─79735 proftpd: (accepting connections)
Nov 19 10:01:36 sftp.kimconnect.com systemd[1]: Starting ProFTPD FTP Server...
Nov 19 10:01:36 sftp.kimconnect.com proftpd[79731]: Checking syntax of configuration file
Nov 19 10:01:36 sftp.kimconnect.com proftpd[79731]: 2018-05-12 10:01:36,656 sftp.kimconnect.com proftpd[79731]: processing configuration directory '/etc/proftpd/conf.d'
Nov 19 10:01:36 sftp.kimconnect.com proftpd[79731]: 2018-05-12 10:01:36,657 sftp.kimconnect.com proftpd[79731]: mod_sftp/1.0.0: unable to use '/etc/ssh/import/ssh_host_dsa_key>
Nov 19 10:01:36 sftp.kimconnect.com proftpd[79731]: 2018-05-12 10:01:36,657 sftp.kimconnect.com proftpd[79731]: mod_sftp/1.0.0: unable to use '/etc/ssh/import/ssh_host_rsa_key>
Nov 19 10:01:36 sftp.kimconnect.com systemd[1]: Started ProFTPD FTP Server.
Nov 19 10:01:36 sftp.kimconnect.com proftpd[79735]: 2018-05-12 10:01:36,697 sftp.kimconnect.com proftpd[79735]: processing configuration directory '/etc/proftpd/conf.d'
Nov 19 10:01:36 sftp.kimconnect.com proftpd[79735]: 2018-05-12 10:01:36,698 sftp.kimconnect.com proftpd[79735]: mod_sftp/1.0.0: unable to use '/etc/ssh/import/ssh_host_dsa_key>
Nov 19 10:01:36 sftp.kimconnect.com proftpd[79735]: 2018-05-12 10:01:36,698 sftp.kimconnect.com proftpd[79735]: mod_sftp/1.0.0: unable to use '/etc/ssh/import/ssh_host_rsa_key>
Nov 19 10:01:36 sftp.kimconnect.com proftpd[79735]: 2018-05-12 10:01:36,717 sftp.kimconnect.com proftpd[79735] 10.17.130.142: ProFTPD 1.3.6c (maint) (built Sun May 10 2020 20:>
Resolution:
[root@sftp backupadmin]# chmod 600 /etc/ssh/import/ssh_host_dsa_key
[root@sftp backupadmin]# chmod 600 /etc/ssh/import/ssh_host_rsa_key
[root@sftp backupadmin]# systemctl restart proftpd
Validation:
[root@sftp backupadmin]# systemctl status proftpd -l
● proftpd.service - ProFTPD FTP Server
Loaded: loaded (/usr/lib/systemd/system/proftpd.service; enabled; vendor preset: disabled)
Active: active (running) since Thu 2018-05-12 10:12:27 PST; 3s ago
Process: 236976 ExecReload=/bin/kill -HUP $MAINPID (code=exited, status=0/SUCCESS)
Process: 79885 ExecStartPre=/usr/sbin/proftpd --configtest (code=exited, status=0/SUCCESS)
Main PID: 79888 (proftpd)
Tasks: 1 (limit: 49018)
Memory: 2.7M
CGroup: /system.slice/proftpd.service
└─79888 proftpd: (accepting connections)
Nov 19 10:12:27 sftp.kimconnect.com systemd[1]: Starting ProFTPD FTP Server...
Nov 19 10:12:27 sftp.kimconnect.com proftpd[79885]: Checking syntax of configuration file
Nov 19 10:12:27 sftp.kimconnect.com proftpd[79885]: 2018-05-12 10:12:27,957 sftp.kimconnect.com proftpd[79885]: processing configuration directory '/etc/proftpd/conf.d'
Nov 19 10:12:27 sftp.kimconnect.com systemd[1]: Started ProFTPD FTP Server.
Nov 19 10:12:27 sftp.kimconnect.com proftpd[79888]: 2018-05-12 10:12:27,988 sftp.kimconnect.com proftpd[79888]: processing configuration directory '/etc/proftpd/conf.d'
Nov 19 10:12:28 sftp.kimconnect.com proftpd[79888]: 2018-05-12 10:12:28,004 sftp.kimconnect.com proftpd[79888] 10.17.130.142: ProFTPD 1.3.6c (maint) (built Sun May 10 2020 20:>
SELinux Permissions:
# Error log
[rambo@sftp-server]# cat /var/log/messages | grep 'FTPTestUser*'
Nov 30 11:58:19 sftp-server systemd[1]: Started Session 32965 of user FTPTestUser.
Nov 30 11:58:19 sftp-server systemd-logind[1223]: New session 32965 of user FTPTestUser.
Nov 30 11:58:19 sftp-server proftpd[95774]: 2020-11-30 19:58:19,297 sftp.kimconnect.net proftpd[228427] x.x.x.x (10.17.131.8[10.17.131.8]): USER FTPTestUser: Login successful
Nov 30 11:58:19 sftp-server proftpd[95774]: 2020-11-30 19:58:19,297 sftp.kimconnect.net proftpd[228427] x.x.x.x (10.17.131.8[10.17.131.8]): USER FTPTestUser: Login successful.
Nov 30 11:58:22 sftp-server setroubleshoot[228515]: failed to retrieve rpm info for /home/FTPTestUser/.esd_auth
Nov 30 11:58:22 sftp-server setroubleshoot[228515]: SELinux is preventing /usr/sbin/proftpd from getattr access on the file /home/FTPTestUser/.esd_auth. For complet e SELinux messages run: sealert -l 870cc3be-bb65-4fe9-ba6b-4d7770341707
Nov 30 11:58:22 sftp-server platform-python[228515]: SELinux is preventing /usr/sbin/proftpd from getattr access on the file /home/FTPTestUser/.esd_auth.#012#012*** ** Plugin catchall_boolean (89.3 confidence) suggests ******************#012#012If you want to allow ftpd to full access#012Then you must tell SELinux about this by enabling the 'ftpd_full_access' boolean.#012#012Do#012setsebool -P ftpd_full_access 1#012#012***** Plugin catchall (11.6 confidence) suggests * *************************#012#012If you believe that proftpd should be allowed getattr access on the .esd_auth file by default.#012Then you should report thi s as a bug.#012You can generate a local policy module to allow this access.#012Do#012allow this access for now by executing:#012# ausearch -c 'proftpd' --raw | audit2allow -M my-proftpd#012# semodule -X 300 -i my-proftpd.pp#012
# Check FTP daemon permission settings
[rambo@sftp-server]# ps -eZ | grep ftpd_t
system_u:system_r:ftpd_t:s0-s0:c0.c1023 95774 ? 00:00:02 proftpd
system_u:system_r:ftpd_t:s0-s0:c0.c1023 228427 ? 00:00:00 proftpd
system_u:system_r:ftpd_t:s0-s0:c0.c1023 233923 ? 00:00:00 proftpd
system_u:system_r:ftpd_t:s0-s0:c0.c1023 234918 ? 00:00:00 proftpd
system_u:system_r:ftpd_t:s0-s0:c0.c1023 235964 ? 00:00:00 proftpd
system_u:system_r:ftpd_t:s0-s0:c0.c1023 235989 ? 00:00:00 proftpd
system_u:system_r:ftpd_t:s0-s0:c0.c1023 235990 ? 00:00:00 proftpd
system_u:system_r:ftpd_t:s0-s0:c0.c1023 236008 ? 00:00:00 proftpd
# Grant FTP daemon full access
[rambo@sftp-server]# setsebool -P ftpd_full_access 1
Check whether proftpd is listening on the correct port:
port=8282
sudo lsof -i -P -n | grep -E "$port.*LISTEN"
[root@sftp-server testAdmin]# sudo lsof -i -P -n | grep -E "$port.*LISTEN"
proftpd 2018 nobody 0u IPv6 42410 0t0 TCP *:8282 (LISTEN)
[root@sftp-server ~]# netstat -natp | grep sshd | grep LISTEN
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 533871/sshd
tcp6 0 0 :::22 :::* LISTEN 533871/sshd
Gabor Kiss
Why are these command necessary?
ssh-keygen -e -f /etc/ssh/ssh_host_rsa_key >> $ftpKeysDirectory/ssh_host_rsa_key_RFC4716_format
ssh-keygen -e -f /etc/ssh/ssh_host_rsa_key.pub >> $ftpKeysDirectory/ssh_host_rsa_key_RFC4716_pub
Where are these files used?
kimconnect
Hello Gabor,
It’s been too long ago since I wrote this. A quick answer would be to generate certain keys in the named formats. Those protocols would possibly be used by the Windows client. I hope this info is still relevant at this time.
Thanks for an interesting question
🙂