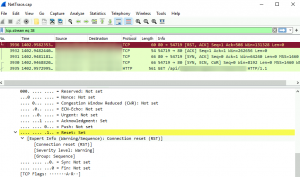
Update: although this is a fun exercise to use Microsoft tools to analyze traffic, it doesn’t work for Guest VMs where NICs have certain features (promiscuous mode) disabled. Therefore, don’t use this method with the expectation that it would somehow enable traffic capture using neutered NICs.
Step 1: Use NETSH command to generate the Trace File
# Init Tracing
$destinationServerIp='2.2.2.2'
$traceFile='C:\tracefile.etl'
PS C:\Users\Administrator> netsh trace start capture=yes tracefile=$traceFile maxsize=1024 filemode=circular IPv4.Address=$destinationServerIp
Trace configuration:
-------------------------------------------------------------------
Status: Running
Trace File: C:\tracefile.etl
Append: Off
Circular: On
Max Size: 250 MB
Report: Off
# Outside of CLI, try to simulate some traffic toward Destination
# When done tracing
PS C:\Users\Administrator> netsh trace stop
Correlating traces ... done
Merging traces ... done
Generating data collection ... done
The trace file and additional troubleshooting information have been compiled as "C:\tracefile.cab".
File location = C:\tracefile.etl
Tracing session was successfully stopped.
Step 2: Convert the .ETL format to .CAP format
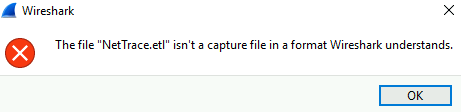
This would happen if you try to open the .ETL using Wireshark
The file "NetTrace.etl" isn't a capture file in a format Wireshark understands.
We need Microsoft Message Analyzer to extract the file. However, it’s deprecated on 11/25/2019 by Microsoft, and its download URLs have been removed by Microsoft. Hence, it can only be downloaded from alternative web-hosts. KimConnect also saves it here for your convenience.
After installed, Microsoft Message Analyzer can open .ETL files and export them into the .CAP format…
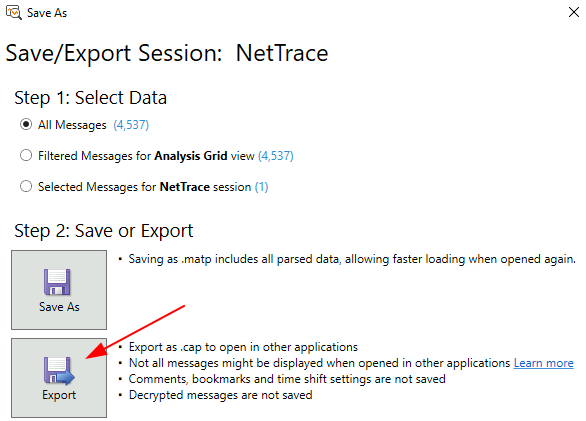
Wrong button – use the other one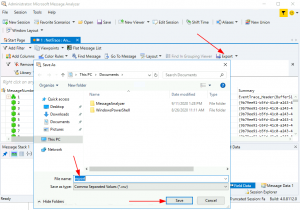
Opps, that’s the wrong button. Try File > Save As > Export
There’s another option, use Matt Olson’s forked version called ETL2PCAPNG: https://github.com/microsoft/etl2pcapng/releases. Once that is installed, run this command to convert the file.
Etl2pcapng.exe $traceFile "$traceFile.png"
Step 3: Use Wireshark to Analyze the packet capture file