function getDuplicatingIfd{
write-host "Checking each relying party trust for any duplicates of identifiers..."
$trusts=Get-AdfsRelyingPartyTrust
$allTrustNames=$trusts.Name
$duplicates=@()
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12
foreach ($trustName in $allTrustNames){
write-host "Checking $trustName..." -NoNewline
#$targetTrust=Get-AdfsRelyingPartyTrust $trustName
$targetTrust=$trusts|?{$_.Name -eq $trustName}
$metadataUrl=$targetTrust.MetadataUrl.AbsoluteUri
try{
$xml=Invoke-WebRequest -Uri $metadataUrl -Method:Get -ContentType "application/xml" -ErrorAction:Stop -TimeoutSec 60
}catch{
#write-warning $_
$xml=$null
}
if($xml){
$endPointReferences=([xml]$xml.Content).EntityDescriptor.RoleDescriptor.TargetScopes.EndpointReference|%{$_.Address}
# $targetIdentifiers=$targetTrust.Identifier # This only returns the existing IFD's that may not have been synchronized
# $otherTrustNames=$allTrustNames|?{$_ -ne $trustName}
# $otherTrusts=Get-AdfsRelyingPartyTrust $otherTrustNames
$otherTrusts=$trusts|?{$_.Name -ne $trustName}
$otherIdentifiers=$otherTrusts.Identifier
#$duplicateIdentifiers=$targetIdentifiers|?{$_ -in $otherIdentifiers}
$duplicateIdentifiers=$endPointReferences|?{$_ -in $otherIdentifiers}
if($duplicateIdentifiers){
write-host "$trustName has these duplicate identifiers"
foreach ($duplicate in $duplicateIdentifiers){
$duplicateTrust=$otherTrusts|?{$duplicate -in $_.Identifier}
if($duplicateTrust){
write-host "$duplicate in '$trustName' and '$($duplicateTrust.Name)'"
$duplicates+=[PSCustomObject][ordered]@{
duplicateIdentifier=$duplicate;
offendingRelyingPartyTrust=$trustName;
defendingRelyingPartyTrust=$duplicateTrust.Name
}
}
}
}else{
write-host " no duplicates..."
}
}else{
write-warning "$trustName is skipped."
}
sleep 1
}
return $duplicates
}
getDuplicatingIfd
Question: what problem does this solve?
Answer: this is a tool to investigate root cause leading to these errors:
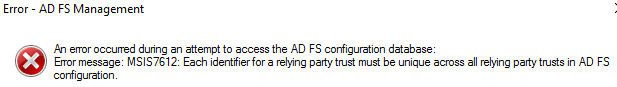
Error - AD FS Management
An error occured during an attempt to access the AD FS configuration database:
Error message: MSIS7612: Each identifier for a relying party trust must be unique across all relying party trusts in AD FS configuration.
Protocol Name:
Relying Party:
Exception details:
Microsoft.IdentityServer.RequestFailedException: MSIS7065: There are no registered protocol handlers on path /adfs/ls/ to process the incoming request.
at Microsoft.IdentityServer.Web.PassiveProtocolListener.OnGetContext(WrappedHttpListenerContext context)
Encountered error during federation passive request.
Additional Data
Protocol Name:
wsfed
Relying Party: Exception details:
Microsoft.IdentityServer.Web.InvalidScopeException: MSIS7007: The requested relying party trust 'https://testcrm.kimconnect.com/'; is unspecified or unsupported. If a relying party trust was specified, it is possible that you do not have permission to access the trust relying party. Contact your administrator for details.
at Microsoft.IdentityServer.Web.Protocols.WSFederation.WSFederationSignInContext.ValidateCore()
at Microsoft.IdentityServer.Web.Protocols.ProtocolContext.Validate()
at Microsoft.IdentityServer.Web.Protocols.WSFederation.WSFederationProtocolHandler.GetRequiredPipelineBehaviors(ProtocolContext pContext)
at Microsoft.IdentityServer.Web.PassiveProtocolListener.EvaluateHomeRealm(PassiveProtocolHandler protocolHandler, ProtocolContext protocolContext)
at Microsoft.IdentityServer.Web.PassiveProtocolListener.OnGetContext(WrappedHttpListenerContext context)