System Engineers must follow the security principle of authentication, authorization, and accounting (AAA) as the framework for controlling access to information technology resources. Authentication and accounting is applied by Active Directory. The administrative element, Authorization is illustrated in the image below.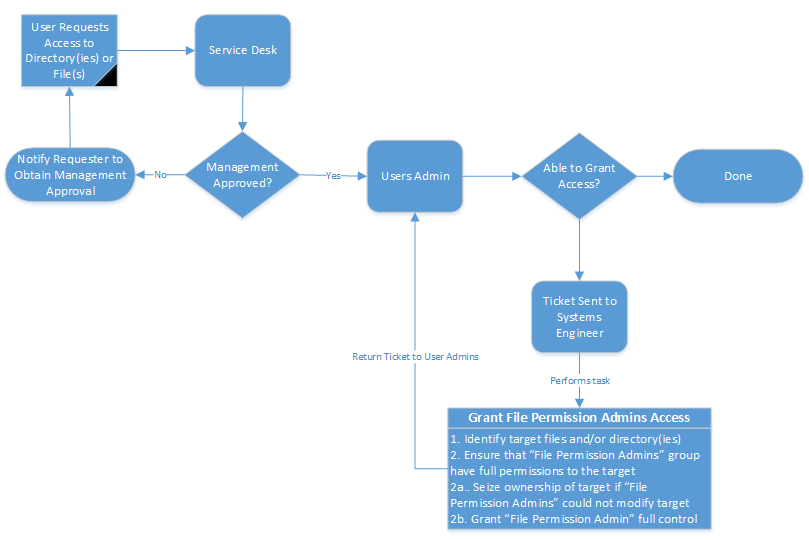
Identify target files and/or directories
It’s necessary to specify the target folders and any child-items that the original requester has been authorized by Management to access. For example, here is a view of a test folder on the network
Ensure that “File Permission Admins” Group has Full access
The “File Permission Admins” would most likely already have access to network directories. One could check this by selecting a file/folder >> right-click on item >> left-click on Properties >> click on Security tab to have this view: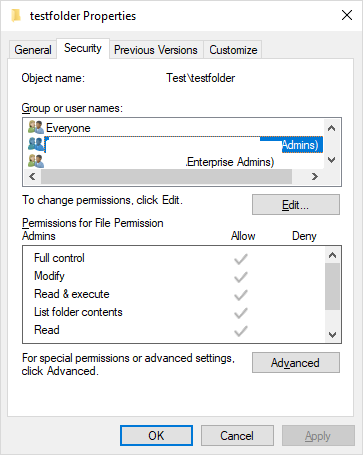
- Seize Ownership
In the rare instances when an object is inaccessible due to “File Permission Admins” being removed from its NTFS permissions list. This would be evidenced with the phrase, “You do not have permission to view or edit this object’s permission settings” when a member of the referenced group tries to access it.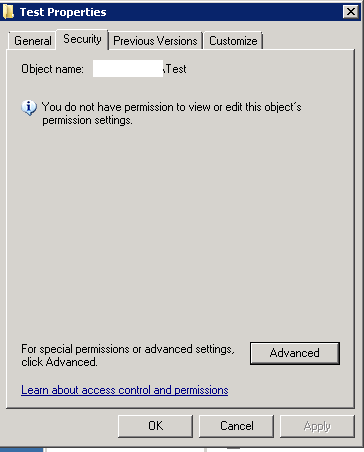
To resolve this issue, the Engineer would click on the Advanced button >> click on the Owner tab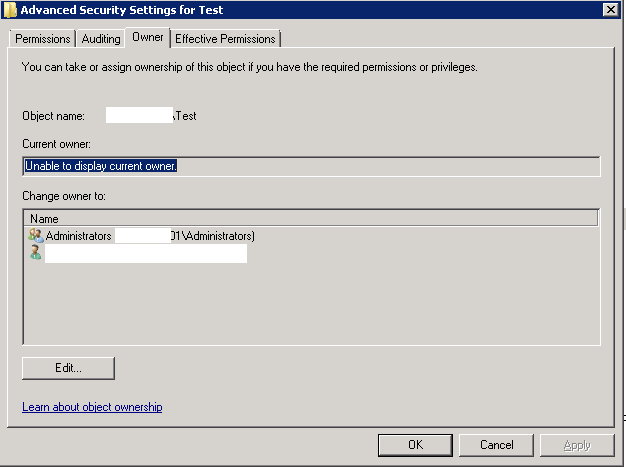
Click on the Edit button >> highlight Administrators group >> put a check mark next to “Replace owner on subcontainers and objects” >> click OK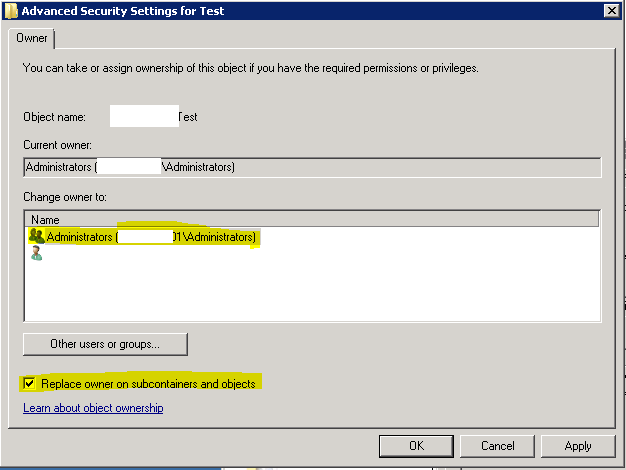
Click OK on the next prompt
- Grant “File Permission Admins” Full control
Once ownership has been seized, NTFS permissions list can be edited to give the “File Permission Admins” control of the object by simply: right-click object >> Properties >> select Security tab >> Edit >> Add “File Permission Admins” onto the list with Full access >> OK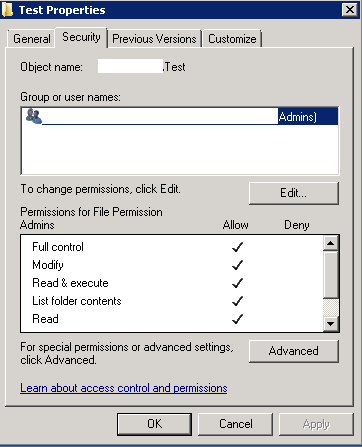
Please be advised that the procedure above would only be effective on the immediate object and any of its children with Inheritance Enabled. If Inheritance has been removed on any items inside the parent folder, its children would reject any access attempts from member of the File Permission Admins. Hence, this error would occur: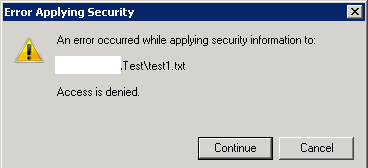
If this happens, it would be necessary to either manually or via scripting to repeat the seizing ownership steps and complete the task.
Once the task is completed. System Engineers would reroute the ticket back to the User Admins queue so that such group can proceed with enabling access to the original requester.