Step 1: Add SSL Certs into the computer information store
Here’s a sample script to import a wildcard SSL cert while login via console (e.g. mstsc /admin):
# Import Cert and get its thumbprint
$certPath="C:\wildcard_kimconnectcom.pfx"
$certPlaintextPassword='PASSWORDHERE'
$certEncryptedPassword=ConvertTo-SecureString $certPlaintextPassword -AsPlainText -Force
$importedCert=Import-PfxCertificate -CertStoreLocation Cert:\LocalMachine\My -FilePath $certPath -Password $certEncryptedPassword
$importedCertThumbprint=$importedCert.Thumbprint
Alternatively, SSL certs may be added to the ‘Web Hosting’ store, instead of the ‘Personal’ store. Per Microsoft, ‘The Web Hosting store works like the Personal store, so all of the existing tools to import and export certificates work the same way. The key difference between Web Hosting store and Personal store is that Web Hosting store is designed to scale to higher numbers of certificates.’ In practice, administrators have a habit of searching for certificates inside the ‘Personal’ store of the local machine. Hence, items inside the Web Hosting store may be missed by unaware admins. Thus, it’s considered a standard practice to ignore this alternative unless the target web server is ultra high density.
There’s the other option to store site certs within IIS ‘Server Certificates’ container. Such feature would automatically pull local machine certs from the usual locations of ‘Personal’ and ‘Web Hosting’, along with capacity to place them in a separate and customized folder path on the server. This offers additional flexibility with the trade off in terms of management simplicity. IIS Server Certificates installation and configuration is outside the scope of this article.
Step 2: Bind SSL Certs to Multiple Sites
Option A: Configure server with multiple IPs
Traditionally, a network end-point can only be identified with one-to-one IP:Port binding. Therefore, this configuration would be straight-forward. Here is a demonstration:
- Overload one IP per domain to be hosted on the web server as per this example:
- Configure server private IP 10.10.10.11 for kimconnect.com
- Configure server private IP 10.10.10.12 for kimconnect2.com
- Create a NAT policy to forward one public IP toward one private IP of the web server. Here’s an example for 2 domains:
- Public IP 1.1.1.1 is mapped to 10.10.10.11
- Public IP 1.1.1.2 is mapped to 10.10.10.12
- Bind each site to a separate private IP
Assuming that IIS has already been installed on the target Windows Server, run inetmgr.exe > navigate to [Server Name] node > Sites > add two (2) websites with names of kimconnect.com and kimconnect2.com > right-click each site > Edit bindings > Add or Edit bindings to resemble these:
- Bind kimconnect.com toward 10.10.10.11 as shown below
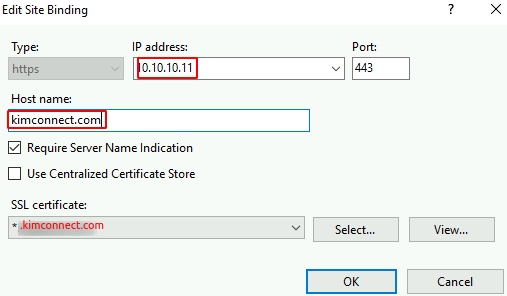
- Bind kimconnect2.com toward 10.10.10.12 as illustrated
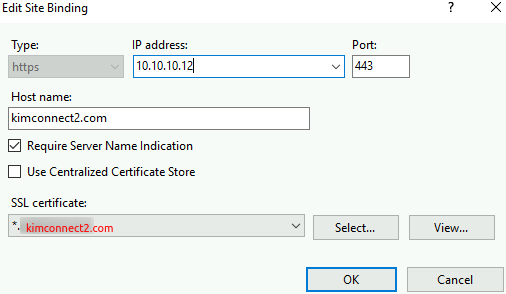
- Bind kimconnect.com toward 10.10.10.11 as shown below
Option B: Use Server Name Indication (SNI) to host multiple sites
Starting with Windows Server 2012, where the certificate store and SNI are part of default IIS installation. There are no specific IIS features that need to be installed from Server Manager. Here is another demonstration to configure IIS 8.0 or higher to use a single IP to host multiple sites with different domain SSL certs.
- On the web server, add records for each domain to be hosted:
- Edit C:\windows\system32\drivers\etc\hosts using Notepad as Administrator
- Add these sample entries:
127.0.0.1 kimconnect.com
127.0.0.1 kimconnect2.com
- Add sites with SNI bindings
One must be mindful not combine traditional SSL bindings (IP:Port) and SNI bindings (Hostname:Port) configurations on the same server. Hence, it is recommended that legacy binding methods be excluded in this approach.
- Bind kimconnect.com toward ‘*’ or ‘All Unassigned’ as shown below
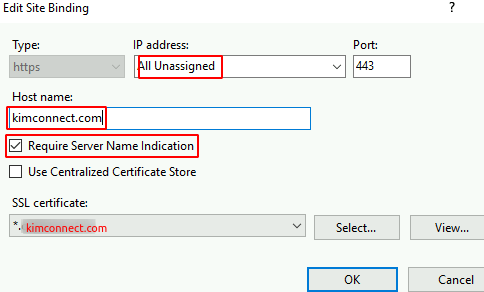
- Bind kimconnect2.com toward ‘*’ or ‘All Unassigned’ as shown below
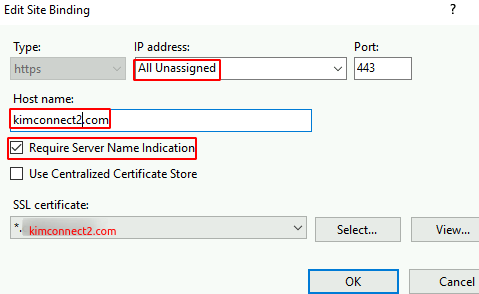
- Bind kimconnect.com toward ‘*’ or ‘All Unassigned’ as shown below
- Verify that the sites are using different SSL certificate hashes
PS C:\Users\TestAdmin> netsh http show sslcert
SSL Certificate bindings:
-------------------------
Hostname:port : kimconnect.com:443
Certificate Hash : 12345abcde
Application ID : {something-something}
Certificate Store Name : My
Verify Client Certificate Revocation : Enabled
Verify Revocation Using Cached Client Certificate Only : Disabled
Usage Check : Enabled
Revocation Freshness Time : 0
URL Retrieval Timeout : 0
Ctl Identifier : (null)
Ctl Store Name : (null)
DS Mapper Usage : Disabled
Negotiate Client Certificate : Disabled
Reject Connections : Disabled
Disable HTTP2 : Not Set
Hostname:port : kimconnect2.com:443
Certificate Hash : 67890fghijk
Application ID : {something2-something2}
Certificate Store Name : My
Verify Client Certificate Revocation : Enabled
Verify Revocation Using Cached Client Certificate Only : Disabled
Usage Check : Enabled
Revocation Freshness Time : 0
URL Retrieval Timeout : 0
Ctl Identifier : (null)
Ctl Store Name : (null)
DS Mapper Usage : Disabled
Negotiate Client Certificate : Disabled
Reject Connections : Disabled
Disable HTTP2 : Not Set